General Explanation
Type: Spyware
Degree of destruction: average
Prevalence: average
What is spyware?
By installing Spyware on your phone, the user’s data security is always under threat and each second, it is possible to be stolen and received by an unauthorized person. Usually, spyware is installed on the phone secretly and out of the user’s sight and performs its actions in complete secrecy. This kinds of spyware collect the necessary data about the user’s activity on the phone or any other data that is necessary and at the right time will send it to another person. Usually, spyware by deceiving users on the internet will be installed on their phone, as a useful and applicant application. The malware collects the information about the user’s activity on the phone such as passwords, credit card information, and other security information such as compressed buttons by keyboard and user’s call list, contact list, sending and receiving a text message, etc.
What is the SpyNote family?
This is a remote access Trojan (RAT). It means, it can remotely and by the server, access all devices that the malware is installed on. The destructive actions that are performed in the user’s phone are items such as: stealing user’s data like messages and contact list, listening to victims conversation, sound recording, controlling camera, attain admin access (Admin), and the possibility to initial calls in the user’s phone.
Technical Explanation
The name of this application is “FollowerInstagram” which is a member of the Spyware family and names “SpyNote”. This application immediately gets control of the Device Admin to help its persistence; so, it does not help the user to delete the application easily. Also, by using AccessibilityServices permission which attains from the user for its application, will attempt to steal complete information from an installed application on the phone, user’s personal information such as calls, send/receive SMS, complete information of the phone, sound recording, taking a photo, receiving geographical situation, etc. after running the application, a service of the type AccessibilityServices, is recalled to attain settings related to accessibility services and the following image will appear to the user. If the user enables the accession for the application, malware will initiate its destructive action without any problem and still keeps its services in the above background (even if the user stops this service, it will restart again after few seconds, and then automatically the application will be closed and its icon will vanish). As surveys, after attaining accessibility services, malware will provide a file that includes a list of the installed application on the phone along with the installation date and package name and will add it in the data/data path. I.e. the application updated will make a list of installed applications on the phone and collect its other desired information, will run once the A application service every 3 minutes, and checks the execution of this service.
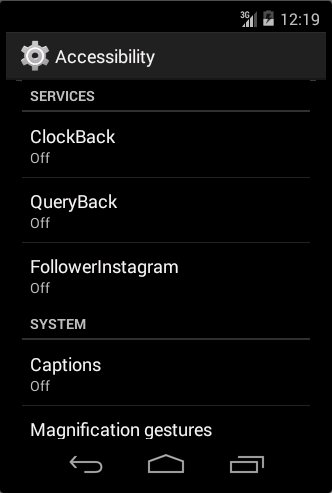
“A” service:
The following destruction operation will happen every 15 seconds:
- Will keep the device on in the background which is executed by running application services using the WakeLock method.
- Because in a special situation such as SafeMode, the WiFi connection will automatically shut down by using WifiLock to keep the device’s wifi connection on.
- Checking the on/off situation of the phone screen.
- Fetching complete information of the user’s phone which includes the follows:
- The device specification (host, ID, device model, system bootloader version number, a trading name of the device, name of the hardware, fingerprint, name of the manufacturer, hardware-software number, etc.)
- OS specification (Android version, SDK version, language, and the current time.
- SIM card specification (IMEI, SIM card serial number, network operator, operator’s name, phone number, and the zip code of the provider country).
- A geographical situation or phone’s locale by GSM (cell phone country code, cell phone network code, cell phone signature, area code of the residence)
- Battery (Battery power status, check how the device is charged (USB))
- WIFI ( service signature, MAC address, velocity, signal quality)
- The volume of the phone
- Checking Bluetooth connectivity status
- Specifies SIM cards with active internet.
- Access to SD card and attain a list of all files in it.
- Access to internal storage and changing its contents (for instance changing name or the file storage paths, change in the size and the existing image frame, etc.)
- Access to call log and fetching its full data (name, number, etc.)
- Checking of being root or not being the root
- Access to the full information of user’s phone SMSs (text of the message, sender/receiver name, sender/receiver number, date, etc.)
- Access to user’s account information in the system (name and the type of user account)
- Access to complete information of phone contacts
- Access to complete information of call history and remove each item according to its specified signature
- Access to complete information of phone contacts and change/remove each item according to its specified name
- Fetching camera settings
- Access to phone camera settings, because each time the rare or front camera is adjusted
- Opening the phone camera
- Creating a list of setScanMode, setFocusMode, setFlashMode, and setColorMode (different modes that adjusted for taking a photo, for instance, Flash, Color, and Scan)
- Taking a photo and checking if the photo is taken right or not.
- Change in device volume, for instance, increasing the voice, if the system’s volume is low or off
- Adjusting the microphone as a sound resource to record voice, recording voice, and storing it in a path in the SD card.
- Possibility of turning the WIFI on or off
- Access to locale status information of the user by GPS and checking it every 5 seconds
- Checking the activation/deactivation of GPS
- By getInstalledApplications it will receive a list of all applications that are already installed on the phone which involves complete information such as first installation date, last update date, application icon, application version, application path, application size, and whether the application is system-based or user-based.
- Checking the special application being installed and open it, if it is installed.
- Attain system policy (principles and rules set for the device) and then initiate the factory reset which deletes all user’s information.
- Initiating a phone call by specific phone number and attain certificate “android.permission.CALL_PHONE”.
- By using send text message() and assign the receiver phone number and the message text, sends an SMS and then checks its send/failed status
- Stealing pressed key information from the user’s keyboard and saving them
- By attaining the “android.intent.action.DELETE” permission and adjust the package name of the desired application, will delete applications.
Finally, this spyware after collecting all its desired information about the victim, will encrypt them and send them to its command and control server “images. myvnc[.]com”.
How to deal with it and disinfect the system
To make sure that the system is safe, install Padvish antivirus and keep its database file and scan it.
Methods of preventing phone infection:
- Avoid downloading and installing any application from unauthorized resources/markets.
- Note the requested permissions, when installing the mobile application.
- Continuously back up your saved data and files.
- Do not use an unofficial version of applications. Applications such as Telegram, Instagram have many unofficial versions and most of them release through Telegram channels.