General Explanation
Type: Rootkit
Degree of destruction: average
Prevalence: low
Used tool: Computrace LoJack
What is Rootkit?
Rootkits will impact destructively on the OS kernel. These changes can hide many functions such as files, processes, Windows internal service, etc. Also, this malware will connect to the server and update its file without the user’s notice. Rootkit’s main activities are changing OS kernel structures, creating destructive drivers, and/or changes in a way that a healthy driver works.
What is Lojax malware?
This malware is related to fancy bear or APT28 and is a member of a campaign of stealing information from the mentioned group. This malware creates a backdoor and a downloader with very high permanence in the victim’s system. For this matter, it is exploiting the anti-theft software security defection belonging to Computrace. These tools which are Rootkit themselves, by adding tools and their permanence elements in the UEFI Firmware, ensure that the original owner is still able to monitor, detect and control the system, even if the malware is theft and clear the memory of the computer completely. This attacking procedure was added to anti-viruses whitelists, concerning the software function. Lojax malware will replace the main command and control server of the main software with the malware element along with its command and control server, by seducing this software and the vulnerability of the previous versions of it and according to being ignored by the anti-viruses, will escape the detection.
Technical Explanation
Lojax acts like Rootkit, which means the program or set of tools that provide access to the admin or network level of the system (while it is hidden). But what makes Lojax special is it is the first detected Rootkit that directly attacks UEFI (Unified Extensible Firmware Interface).
Briefly, UEFI is the alternative to BIOS in computers. Since both are members of Firmware, it is being controlled in a Flash drive with SPI protocol and maintained in the motherboard or system mainboard, and just like BIOS includes necessary instructions to boot the system and control computer chips. This means the UEFI function does not relate to OS.
According to the mentioned cases, Lojax uses a vulnerability in the Computrace LoJack tool. This software which prior, which is installed in most PCs (Laptops) sends some information about the place of the laptop and also allows the files to be blocked or deleted if being theft. Since this is an anti-theft mechanism, LoJack has been designed in such a way to be still on the laptop even if the OS is installed again, because these cases are elements that thieves usually change after stealing a laptop.
Signs of infection
There will be nothing visible in the system except secondary signs because all malware actions perform when boot. When OS is booting, malware will hide its tracks.
Explaining the function
LoJack malware by seducing the anti-theft system process creates and protects its backdoor in the victim’s system, that to do this, it must disorder the connection between the small agent and its server. The address of the command and control server in the small agent is added almost insecure. The content of the address is binary xor. The first 4 byte is the IP and the rest of them is the URL. Since there is no survey and control over this address, any agents with access at the writing level on the Windows directory can change this address and as a result, leads to command and control server forgery.
Of course, you should note that this malware does not hostage LoJack (the possibility that it is being installed on all systems is low), but imitate its actions with exclusive Rootkit, hence it will escape detection by being in the whitelist.
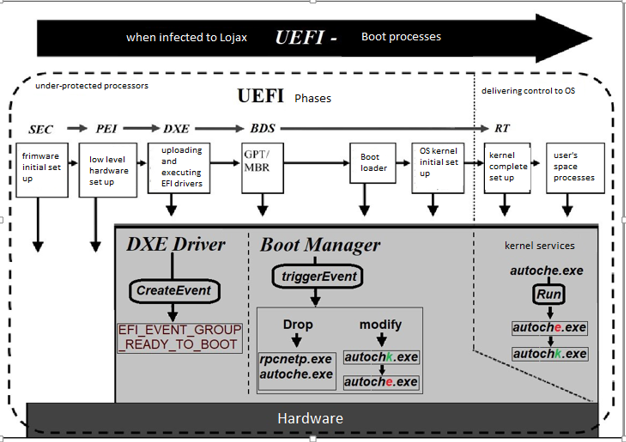
To access hard partitions it uses NTFS DXE drivers. These drivers upload by default before the Boot Manager appears. In infected systems, one of the drivers has been hacked and performs destructive actions. The destructive driver creates an Event in the system named: EFI_EVENT_GROUP_READY_TO_BOOT. This event will send a signal to the driver when the boot procedure reached the stage to choose the device or BDS (Boot Device Selection), so can proceed with its destructive operation. After reaching to BDS stage, Boot Manager by activating CallBack with the secDEX driver will initiate the malware starts. The general procedure of malware action after uploading the driver and activating the event is as follows:
- secDEX writes two files in a Windows partition: autoche.exe and rpcnetp.exe
- the content of the BootExecute registry are as follows:
You must consider that Autochk.exe always checks the hard partition’s health before the booted OS. In the infected system, the autoche.exe application will replace with the healthy application by a registry key.
- The destructive “autoche.exe” application is used to maintain a small agent or rpcnetp.exe. This application despite the similarity to the main autochk of Computrace is different than that. Contrary to the main application, this application cannot replace Windows autochk, but changing the registry forces Windows to use itself. Also, the duty of copying a small agent in the malware is on Rootkit, not this application.
- The destructive “rpcnetp.exe” application or small agent which is possibly installed by the Rootkit before booting Windows, must connect with the command and control server. The above application can download Trojans and other destructive applications, however, no such thing has been viewed. The name and IP list of the command and control server in current versions are as follows:
| No. | IP | URL |
| 1 | 185.144.82[.]239 | ikmtrust[.]com |
| 2 | 185.77.129[.]106 | secao[.]org |
| 3 | 93.113.131[.]103 | sysanalyticweb[.]com |
| 4 | 185.94.191[.]65 | webstp[.]com |
| 5 | 86.106.131[.]54 | elaxo[.]org |
| 6 | 103.41.177[.]43 | remotepx[.]net |
| 7 | 185.86.149[.]54 | lxwo[.]org |
| 8 | 80.185.86[.]148 | rpcnetconnect[.]com |
| 9 | 103.41.177[.]43 | remotepx[.]net |
| 10 | 80.103.41[.]177 | remotepx[.]net |
| 11 | 77.129.106[.]115 | secao[.]org |
| 12 | 46.21.147[.]71 | regvirt[.]com |
| 13 | 185.86.151[.]104 | jflynci[.]com |
| 14 | 185.86.148[.]184 | rpcnetconnect[.]com |
| 15 | 185.86.148[.]84 | rdsnets[.]com |
In the following image, you can view the process of booting:
How to deal with it and disinfect the system
The first solution to prevent this malware is using Secure Boot. Since the used Rootkit of the malware is not signed properly, SecureBoot, which is only allowed to upload signed cases can prevent this infection. However, it is possible that regarding using permitted drivers, this malware passes this blockage. If system software is equipped with the fourth generation of Intel Core processors and higher, you can prevent UEFI Flash from infection, even if it is infected it can stop system boot.
If the system is infected, the SPI and Firmware memory must be flashed and installed again. If for any reason you will not able to prevent this, there is no way except to change Motherboard.
Padvish antivirus will detect this malware and remove it from the system. To prevent entering these kinds of malware into the system it is recommended to avoid clicking on suspicious links and always scan attach files in emails before execution. Also, always keep the OS and antivirus up to date, if applicable.