General Explanation
Type: Adware
Degree of destruction: average
Prevalence: average
What is Adware?
Adware is advertising malware that results in showing ads or appearing multiple banners in your system and encourages you to buy a product or use its services. Programmers of this malware, earn money by using related codes that send notification services to applications to show ads. They are attempts to encourage more people to use their applications, by adding them to android markets.
What is the HiddenApp malware family?
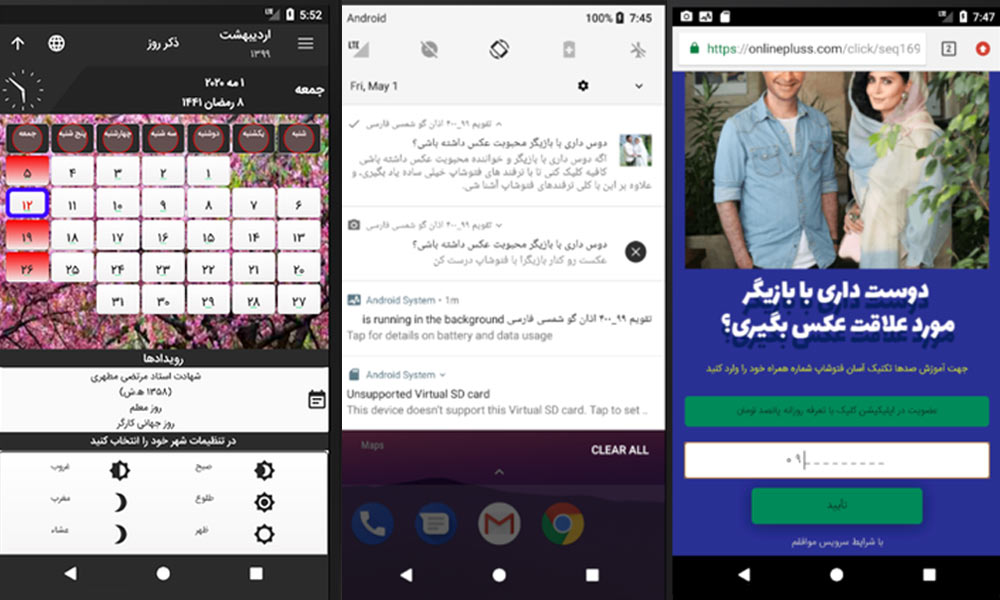
HiddenApp adware in the background of send notification services will show advertising notifications to the user. If you click on each one of these notifications, malicious codes will run on the user’s phone, without the user’s notice. Also, this adware tries to download other suspicious or infected applications on the user’s phone. Additionally, this adware acts like a botnet and for reaching its malicious goals, it uses the command and control server of notification-sending service providers for android phones (Pushe, Cheshmak) as its command and control server.
Technical explanation
After initiating the main application activity, the application is run in the background and will be checked by sending receivers from OS to applications.
Here is an example of sent receivers:
The application will check the status of the service, by receiving each one of these messages from the Android OS system. Because the android OS kills the unused services in the background, programmers will use Alarmmanager class for special modes that users do not use on their phones, so that the service of their application remains in the background. This class is used as a type of timer watch and when the service is not running, it will check and initiate it again (“BROADCAST_RESTART_APP”).
In the code review, it was found that this malware has two classes related to handling notification-related cases. A class named MyPusheListener which inherits from PusheListenerService class related to the Pushe service and the other class CheshmakFirebaseMessagingService inherits from Cheshmak class and runs and decides most of its malicious operations by using the existent data in the received JSON and these two classes. The sent Json by notification, has two keys with different values each one of them is for a special occurrence event and if the only user clicks on the notification, it will be executed. Notification sends from Pushe service, causes follow cases to execute:
- Checking the name of the application: the goal of this review is accessing the whole information about the application which is installed on the system. If the return value is not the desired APK version or is being updated, the updated APK file will be downloaded according to the specified address in the “link” parameter and will be added to the download directory of External_stroage.
- It will refer the user to the specific page on Instagram:
private void b(String paramString)
{
paramString = new Intent(“android.intent.action.VIEW”, Uri.parse(paramString));
paramString.setPackage(“com.instagram.android”);
paramString.addFlags(268435456);
try
{
paramString.addFlags(268435456);
startActivity(paramString);
return;
}
catch (ActivityNotFoundException paramString)
{
paramString.printStackTrace();
}
}
- The goal is to show an image to the user with the existent address in the “strlink” parameter.
private void a(String paramString1, String paramString2)
{
System.out.println(“imgshow”);
Intent localIntent = new Intent();
localIntent.setClass(this, imgshow.class);
localIntent.putExtra(“strimglink”, paramString1);
localIntent.putExtra(“strlink”, paramString2);
localIntent.setFlags(268435456);
startActivity(localIntent);
}
- Showing an ad dialog to the user.
- First, it will check if the telegram application “telegram. messenger” is included in the list of the installed application on the user’s phone. If telegram is installed, it will refer the user to a specific page on Telegram and will open it. whether to what link the user will connect, is inside the param string parameter as sending input to the Uri. parse() function. This is not only happening for the official telegram version but it will check the list of other unofficial Telegram applications on the phone either.
private void g(String paramString)
{
Intent localIntent = new Intent(“android.intent.action.VIEW”, Uri.parse(paramString.toString()));
localIntent.setPackage(“org.telegram.messenger”);
if (!c(“org.telegram.messenger”))
{
if (c(“com.hanista.mobogram”)) {
paramString = “com.hanista.mobogram”;
}
for (;;)
{
localIntent.setPackage(paramString);
break;
if (c(“ir.persianfox.messenger”))
{
paramString = “ir.persianfox.messenger”;
}
else if (c(“ir.ilmili.telegraph”))
{
paramString = “ir.ilmili.telegraph”;
}
else if (c(“com.mehrdad.blacktelegram”))
{
paramString = “com.mehrdad.blacktelegram”;
}
else if (c(“com.baranak.turbogramf”))
{
paramString = “com.baranak.turbogramf”;
}
else if (c(“com.telegram.hame.mohamad”))
{
paramString = “com.telegram.hame.mohamad”;
}
else if (c(“ir.felegram”))
{
paramString = “ir.felegram”;
}
else
{
if (c(“ir.rrgc.telegram”)) {}
while (c(“ir.rrgc.telegram”))
{
paramString = “ir.rrgc.telegram”;
break;
}
if (!c(“com.avina.tg”)) {
break;
}
paramString = “com.avina.tg”;
}
}
}
localIntent.addFlags(268435456);
try
{
localIntent.addFlags(268435456);
startActivity(localIntent);
return;
}
catch (ActivityNotFoundException paramString) {}
}
List of applications:
| Application name | Package name |
| Telegram | Org.telegram.messenger |
| Mobogram | Com.hanista.mobogram |
| Telegram Farsi | Ir.persianfox.messenger |
| Graph Messenger | Ir.ilmili.telegraph |
| Black Telegram | Com.mehrdad.blacktelegram |
| Turbogram | Com.baranak.turbogram |
| All function telegram | Com.telegram.hame.mohamad |
| Felegram | Ir.felegram |
| Farsi orange telegram | Ir.rrgc.telegram |
| Rasagram | Com.avina.tg |
- Opening a specified link and pushing the user to be a member of added-value services.
Sent notifications from Cheshmak services will cause to following actions:
- Downloading a specified application in the user’s phone and also add that file in the path of “ExternalPublicDir”.
- Review whether a specified application is installed on the user’s phone and if it is not, the file must be downloaded from the sent encoded address in the JSON file.
- Opening a specified (ad) link for the user.
- Opening a specified page in Telegram messenger; if Telegram is not installed on the user’s phone, by referring to the web-specified address, the ad link will be open (probably using the web version of Telegram is attempted).
- Showing a dialog box to the user; the user by clicking on the install button in the notification will download a specified application from a specified address in android app markets. These addresses are from Café Bazar, Myket, Iran apps, and google play.
How to deal with it and disinfect the system
To ensure that the system is not infected, install the Padvish anti-virus database file, keep it up to date, and scan the anti-virus.
Method of preventing phone infection:
- Avoid downloading and installing the application from unauthorized resources.
- Note the desired permission, when installing the application.
- Constantly back up the stored files and data.
- Do not use unofficial versions of any applications. Applications such as Telegram and Instagram have many unofficial versions and most of them are released through the Telegram channel.